31 January 2024
Don’t get phished!
Malicious messages are on the rise. Industry experts estimate that such attacks have risen over 6- to 10-fold since the beginning of the COVID19 pandemic in 2020. In iBizify’s opinion, these threats are now the most significant, beyond traditional malware and direct attacks.
Whilst most attacks are delivered by email, such messages can be delivered via almost any medium including email, text, social media, WhatsApp and even phone calls.

These threats deceive people into revealing sensitive information such as passwords, bank account details, etc. and can be categorised into two variations:
- Phishing: Generalised attacks that are usually sent en masse. The purpose being to catch victims by targeting large numbers within each campaign.
- Spear Phishing: These are highly curated and sophisticated. They usually include more specific information about the targeted individual, such as mentioning several names of people known to the individual, specifying their company name, bank information or specific online services they are known to use.
Seemingly benign phishing attacks are often used to gather intelligence to prepare a Spear Phishing attack.
How do I spot a Phishing email?
THINK BEFORE YOU CLICK! Look out for…
- Urgent, Important, Overdue, flagged as important
- Requests for personal information
- File attachments that lead to very genuine-looking login pages
- Invoices, voicemails or messages waiting for you
- Missed deliveries, parcel tracking
- Your account or password has expired or blocked
- Your computer or account is infected
- Social cues "saw you in this video", "did you really do this?!", etc.
- Claims to be from Apple / Microsoft / Google / Amazon tech support
If you are still convinced the message is genuine, and feel the need to click:
Hover over links to reveal the actual destination. Look at the domain name – the bit before the .com, .co.uk, etc. If the email claims to be from Lloyds Bank, but the destination domain is not a Lloyds domain but rather amazonaws.com (a commonly used tool for phishing) or some other unknown value, then do not click!
Consider not using the email links at all, and instead contact the provider directly using known-good contact information.
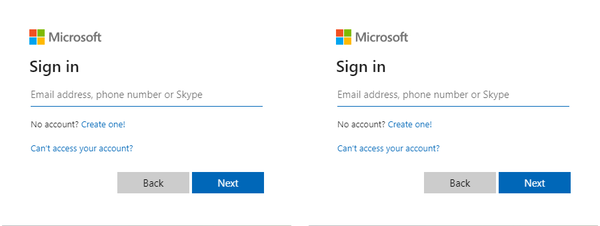
Can you spot the difference between this genuine sign-in page and the fake one?
Be aware
Malicious messages may appear to be from someone you know, they may even include your friend or colleague’s name and contact details. Never assume a message is safe even if it is from a known contact.
You will never get legitimate messages direct from Microsoft / Apple support claiming they have detected malware on your device (or similar).
Never let anyone connect to your device unless you truly know who they are, and have especially good reason to do so.
Be secure
- Maintain your software and devices with the latest updates. Install them promptly and frequently. Don’t forget your PCs, Macs, Android, iPhone, iPads
- USE MULTIFACTOR AUTHENTICATION on any online accounts that you can.
For example, if you use Microsoft online services, set up “Microsoft Authenticator” on your phone. Doing so will help to protect your account even if your password is compromised - ALWAYS use complex passwords for all your online services
- NEVER re-use passwords on multiple online accounts
If you do, if one is compromised, its details will be stored on a database and then used to successfully attack your other accounts (this happens more than you think!) - AVOID using your business email address to sign up for circulars/newsletters or other bulk mail. Doing so shares your email address more widely and makes it harder to filter genuine email. If you want these messages, consider instead setting up a free personal email address to receive them.
- Discuss with your IT provider about how to filter and minimise these attacks
Use password management
Here is an example of a strong password:
8Q{{a>0g13C9gi29.<yW
Could you remember this and type it in every time? Probably not, which is a solid reason to make use of a reputable password manager such as Keeper.
Report attacks
For the collective sake of your organisation and others, always report malicious emails if you can. Doing so will help prevent others from receiving the same.
- Check with your organisation’s IT administration or support to see if they have a reporting mechanism.
- Common email tools such as Outlook have dedicated report buttons that you can use. Simply select the message and click the Report Message button.
- If you don’t have these options, consider forwarding the message to report@phishing.gov.uk for the National Cyber Security Centre (NCSC) to review.
Caught out?
If you believe you may have shared your login details or other sensitive information, please change any relevant passwords and contact the host of the service for advice. If you are part of an organisation, then inform your manager. If you shared financial information, contact your bank or card provider as soon as possible. For more information on what to do please visit https://www.ncsc.gov.uk/collection/phishing-scams/what-to-do.
Need help?
If your organisation is an iBizify Premium subscriber, we will already be supporting you in securing your systems and helping your staff to work safely.
iBizify offers a wide range of managed security tools and services from backups, and password managers to vulnerability and endpoint assessments, and online security baselining.
If you have any questions or would like to discuss your IT security, then contact us by scheduling a call at https://ibizify.net/callback/
22 August 2023
How to set up Microsoft Authenticator
These instructions assume you already have a Microsoft 365 account set up with a username and password. They are aimed at iBizify Microsoft 365 customers.
- Sign in to your Microsoft 365 account at office.com.
- Click your profile icon in the top-right, then View account.
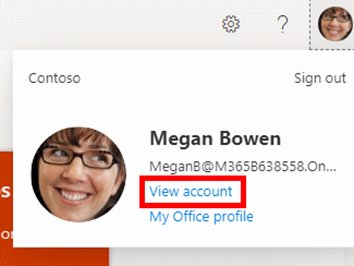
- Under Security info click UPDATE INFO >
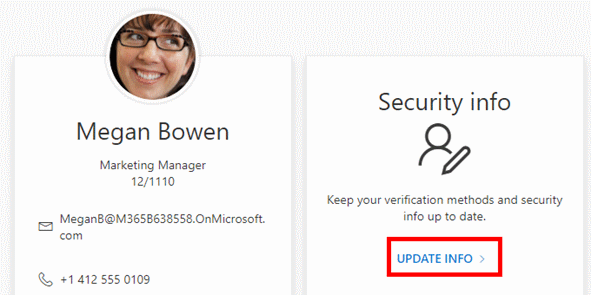
- Click Add sign-in method
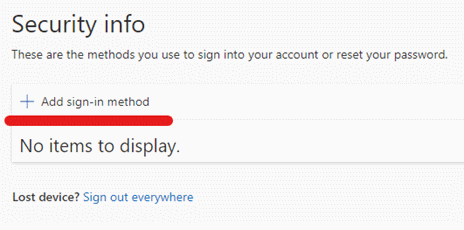
- Select “Authenticator app”, then click Add.
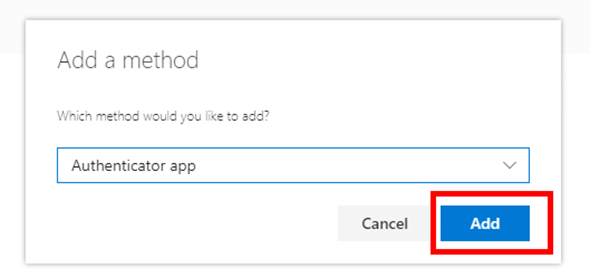
- In your phone’s app store, search for and install “Microsoft Authenticator”.
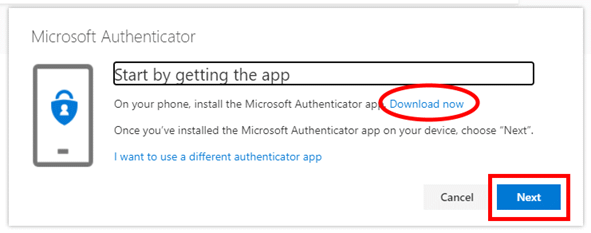
- Click Next, then Next again.
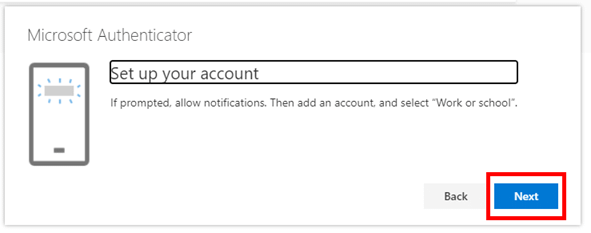
- On your phone…
Open the Authenticator app.
?? If you have not used Authenticator before, you might first be prompted to sign into a personal Microsoft account to facilitate backing up your Authenticator codes. If you have a personal Microsoft account, we recommend doing this. If not, you can create one or skip this process.
- In the menu, click Add account.
- Choose “Work or school account”.
- Tap Scan a QR code.
- Use your camera to scan the QR code presented on your computer screen.
?? Your phone may ask you to give Authenticator permission to use your camera. You need to allow this.
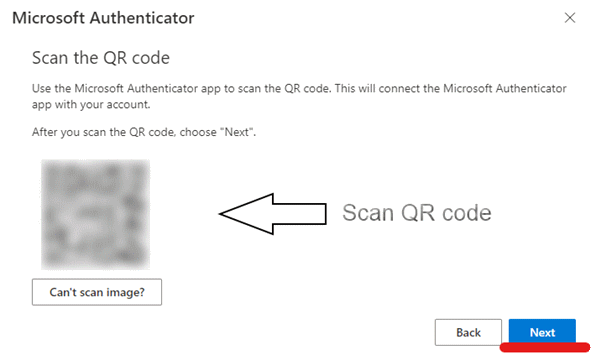
- On your computer, click Next. Note the two-digit number presented on the computer screen. In this case, 28.
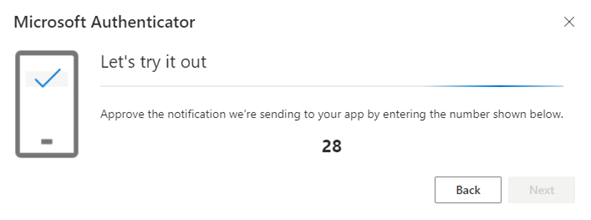
- Back on your phone, the request will pop-up either on your phone screen or as a notification.
- Tap on the notification if necessary, then enter the two digit number, then tap YES (or the tick button) to approve the login.
- Your computer will now automatically confirm the approval. Click Next.
- Setup is complete.
In future when you sign into a new device, or periodically thereafter you may be asked to approve a sign in request on your phone after having entered your password.
?? If you ever receive a sign in approval on your phone when you are NOT signing in, report the incident to your administrator or support team.
01 March 2023
Understanding your Microsoft 365 email quarantine
The Microsoft 365 “email quarantine” captures incoming spam, phishing, malware and other unwanted email in a secure container. Such emails are locked in the quarantine either until they expire, or you request they be released.
Learn more about malicious emails, phishing, and what to do about them.
We are in the process of reconfiguring the quarantine to capture more regular threats for our iBizify-managed Microsoft 365 clients. We are also working to prevent the delivery of certain file attachment types (such as HTML) that are regularly used to carry phishing attacks.
The side effect of this is that on occasion you may find that some benign email that you did want to receive may not reach your Inbox or even your “Junk mail” folder. To counter this, where there is doubt of the legitimacy of one or more email items, you will receive an email from quarantine@messaging.microsoft.com that look like this:
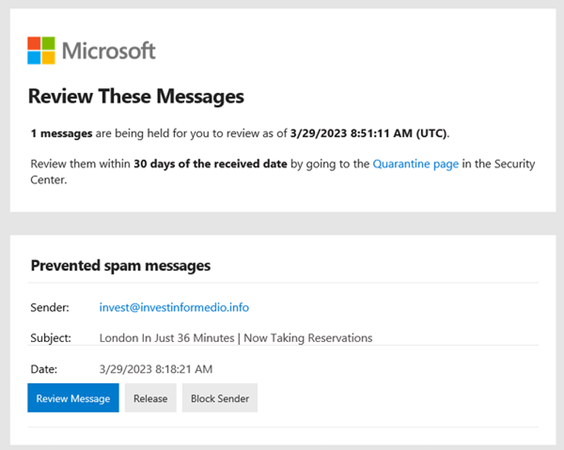
The irony isn’t lost on us, that this important message does look like a phishing email. Check that it is indeed from quarantine@messaging.microsoft.com before you click!
In this notice, you can see who sent the quarantined message, when it was sent, and what the subject is.
You have four ways to respond:
1. Ignore it. The quarantined email will be deleted after thirty days.
2. Review Message. If you aren’t sure about it, you can look at the message safely by previewing its contents.
3. The message will be released to your mailbox.
4. Block Sender. In this scope, this option won't actually have any affect because the sender is already blocked from reaching your inbox.
27 March 2022
Development and consultancy hours - simplified
We've simplified our pricing structure for development and consultancy services.
Previously only usable for technical support, service packs can now also be used for software / web development, consultancy / technical writing, and reports.
We simply apply a 1.5 multiplier. For example: 2 hours of development would use 3 units; 5 hours would use 7.5 units.
This means it’s now really easy to purchase one or two ten-packs and use them for a variety of projects and support all through one simple billing process.
11 September 2021
We have a new logo
Out with the old and on with the new...

This iBizify is simpler, bolder and more rounded than the old one.
21 July 2021
We have moved
We completed our move to Claydon House in Aylesbury recently - a new workspace to increase productivity, create a professional meeting environment, a bit more desk space, and room to grow. We are very pleased with the results.
Conveniently, our office address now matches what has always been our postal address. You can find our location on Google of course.
19 December 2020
What to look for in a PC for your small business
When you need to get a new computer for your business in a hurry, it can be tempting to grab a cheap deal from a local store or from the top of Google. After all, many devices look alike – they have screens, keyboards, more or less features. However, what you buy and how much you spend will dictate a great deal about the experience you get with that device months or years after the purchase. Here we discuss what to look for in a business PC and how to avoid pain later.
This article assumes you are looking for a Windows-based PC for general, everyday use. If you use specialist or particularly demanding software you should consult the vendor to ensure the specifications are appropriate. We discuss Apple Macs below. Call us for advice if you are uncertain.
How much should I spend?
The short answer is as much as you can or want to. A more helpful question is “what is the minimum I should spend?” because this is where things go wrong. There is a wealth of low-end PCs available. Many of which look great from the outside, often the same or better-looking than their more expensive counterparts. We’ll discuss this more below, but in the meantime, here is a rough guide based on 2018 laptops:
Minimum spend for a sensible business laptop: £700 - £1,000 + VAT
Recommended spend for a business laptop: > £1,100 - £1,400 + VAT
Minimum spend for “luxury”, a convertible or more powerful laptop: > £2,000 ++
There is also a huge variety of options in the “luxury”, convertible or super-powerful market. We are going to focus on everyday business laptops here.
Why not buy a cheap laptop?
Cheap laptops are often fine for general home use, if you don’t expect many years of service. For business use, you will want something dependable that is not going to demand a lot of time and money for service or repair. Here is why:
You'll discover the limitations later
Cheap laptops often shout the same big numbers as their more expensive counterparts, such as processor speed and amount of memory. What they don’t shout about is the cheap and slow variants of components used. It is usually the things you cannot see on the device, and the things not mentioned on the specification sheet that will let you down.
For example, it might shout about having 2,000 GB of storage – but you will probably find it is an old, slow hard disk or a cheap “hybrid” drive, which you will quickly want replaced. It might have an Intel i5 or an i7 – but it’s an old, power-hungry variation that will be slow and kill the battery.
They lack business-grade features
Cheap laptops cut out anything that isn’t an absolute requirement for pretty much anyone. This means, business features get the chop. You might not feel you need these, but – further down the line – you will. This often means costly upgrades later.
They are not built to last
When you look “under the bonnet” of a cheap laptop, you start to see where they cut the cost in production. Weak structures, poor strain relief, and things packed in in such a way that makes it hard or impossible to repair, service or upgrade. This not only means the device will be unlikely to cope with a bit of rough and tumble, but also that when you need more from it (and you will!) – it won’t be able to help you.
We find that customers who purchase a cheap laptop rarely get more than one or two years of useful life from them. A well specified laptop can usually last at least three times that! When you look at it this way, you can realise that a cheap laptop is actually an expensive laptop.
They are not serviceable or upgradable
Cheaper laptops often have everything hard-wired in and are difficult or impossible to disassemble. This means if things go wrong, you are likely to need to buy a new laptop rather than be able to repair it.
Ironically, high end / luxury devices also suffer from this issue, but for different reasons – because they are generally built to be compact, light and fancy looking over being serviceable. This is something to consider if you are in the market for a high-end device – be sure you can afford the servicing!
They come with annoying software and exclude what you need
Operating systems and software cost money. To save money, cheap laptops employ two key tactics:
- Use cheap “home” software that lacks business features, such as Windows Home edition
- Accept payments for getting everyone’s junkware on to your laptop. As soon as you start, you are bombarded with useless messages, advertising and a slow, junked up device before you have even started
Both points often mean that service and upgrades are required before the cheap laptop is useable for business – money better spent on a business-grade PC.
What to look for in a business PC
- Look at the price. If it seems too good to be true, then it probably is – especially if it’s below the minimum amount mentioned above
- Look for features that only typically exist in a business PC. I like to look for a “Trusted Platform Module”, or “TPM”. These internal devices are rarely discussed, but they do permit extra security measures and make things like data encryption easier to handle. It is rare to see these in home laptops, so the presence of one in the specification often means you are on to something good!
- Make sure the processor isn’t ancient. Get the exact model name of the processor, and look it up on Wikipedia. Make sure it isn’t years out of date
- Look for fast storage. If it seems to have a very high capacity – like 1 or 2 TB, and isn’t tremendously expensive – it probably has a slow, traditional hard drive. Look instead for an SSD – a Solid State Drive. You’ll get less storage, but it will mean Windows and your apps will load in seconds rather than minutes
- Check its build quality. The sad truth is more serviceable, business-grade PCs do tend to be uglier than their less serviceable counterparts. You must make a choice – go for “middle of the road+serviceable”, or “high end+less serviceable”. For the latter, get insurance or be prepared for service bills. Just don’t go for cheap “low end+unserviceable”!
- Get Pro software. If the device comes with a “Home” edition of Windows, or has a huge long list of useless bundled software – avoid! You will quickly find it lacks what you need and doesn’t perform terribly well, resulting in the need for costly upgrades and service
- Don’t base your requirement on what you need today – consider what you will need in a year or two’s time
- Consider service costs. Mid-range PCs are the lowest cost to service. Low-end and high-end PCs are the least serviceable. If you buy a PC that is not easily serviceable, then consider the extra servicing costs in your future IT budget.
- Check you like it! If possible, have a look at the display and try out the keyboard. These are often a matter of personal taste, so no specification will tell you whether you will like them or not
What about desktop PCs?
In this article we have focussed on laptops as they are most common. However, don’t forget about desktop PCs.
You typically get a lot more for your money in a desktop, and they are usually far more serviceable and will provide many more years of service. You can also easily add / upgrade the displays, change keyboards, add storage etc. You can also “hard-wire” them in so you can have a fully reliable cabled connection to your network without dependency on WiFi, for example. A desktop tends to be more dependable and “ready to go” without fuss – which can better suit some work scenarios.
If you don’t need the portability, then see what desktop you can get for your budget, whilst observing the above points.
What about Macs?
If you prefer Macs then in many ways your options are far simpler. Simply visit https://www.apple.com/mac/ and take your pick. Consider:
- How much power do I need? Want more powerful? Then look to the chunkier devices!
- What form factor do I need? If you want a desktop then look to the iMac series and the Mac Pro
Macs tend to be more expensive vs. their PC counterpart, and generally they are not as serviceable / repairable as mid-range PCs (but quite equivalent in the high-end market).
Whether you should choose a Mac or a PC is an endless, unresolvable argument. Why? Because it’s down to individual choice, and down to whether the software you want lives better on one or the other platform. You can pretty do anything you like on both. Choose which you prefer and don’t listen too much to what others say.
In conclusion
When considering what to purchase, it’s important to stop and think carefully about your needs vs. what is available for your budget. Avoid the plethora of cheap home laptops to get the most return from your investment.
Need matchmaking?
iBizify support is available in both an ad-hoc ‘pay-as-you-go’ basis at £40 per hour (discounted pre-pay packs available) as well as customised monthly packages. These can be used for “how-to” as well as technical support.
If you need help finding the perfect PC for you, then discuss your needs with us and we will find options for you from the whole market.
If you'd like to find out what can be achieved, then please book a call back.
This article was written by Steve Munden of iBizify.net
True False True 2020-12-19 12:53:00 2024-02-09 12:43:39 0 0 what-to-look-for-in-a-pc-for-your-small-business
15 September 2020
Why you should get to know Microsoft Teams
Microsoft claims that Teams is its fastest growing business app in its history. As of 11th March 2020, Microsoft reported 32 million daily active users but this jumped by 12 million to 44 million daily active users in just one week amid the ongoing coronavirus pandemic. By April the number was 75 million. Teams is used by organisations large and small and has come into its own as businesses suddenly adapt to working remotely. So, what makes it so popular?
Teams is Microsoft 365’s baby
Being one of the most widely used business tools in the world, it is highly probably you have heard of Microsoft 365 (formally Office 365) - or are already using it. Microsoft 365 is a subscription-based service providing a collection of software and cloud services that offer a highly adaptable, scalable and reliable solution to business productivity and collaboration needs.
Launched in 2011 Microsoft 365 has grown enormously and whilst under constant development, new features and tools have appeared monthly. This is both good and bad. It is good because the value of your subscription just keeps improving and the service becomes more useful. It can be a bad thing due to difficulties in keeping up with the changes and being sure you are making the best use of your investment. It can be hard to know how best to use the tools in context with the rest of your team – especially as individuals can often have different methods of working.
Microsoft Teams is the answer. Part of Microsoft 365, and now available as a stand-alone solution it offers a single “pane of glass” that provides access to (almost) everything. Helpfully it runs on Windows, Mac, Linux, iPhone and Android (or failing that there is the web browser!).
How does it work?
Created in 2016 Teams is centred around members organised within defined teams and channels. For example, in a small business you might have sales, marketing and finance teams. Within the sales team you might have a channel for proposals and prospects. The marketing team might have channels for certain campaigns, asset libraries, etc.
Divided into “tabs,” each channel includes a conversation tab where team members can “chat” together (instant messaging style), and a Files tab. The Files tab is where any documents (such as Word or Excel sheets) can be uploaded, shared and collaborated upon by the team, and easily referenced within chat. Files can be edited right within Teams using the power of Office Online, all without having Word etc. installed (though if you do have these you can instantly launch into them for your full Office editing experience). Teams keeps everything in one place, reduces “chat over email” and other clutter.
At the top of Teams is an incredibly powerful search, command and contact box – where just about anything (and anyone) you could need is a few taps away…and indeed it works very well (sadly unlike some of Microsoft’s other search offerings).
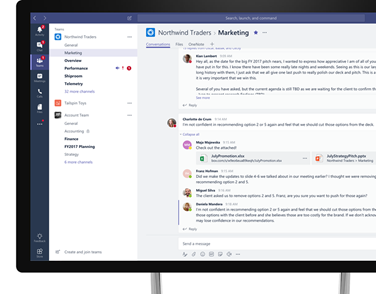
The methodology of Teams goes a long way and can be applied effectively to a vast array of needs. It can be adapted to suit many individual organisational approaches. However, the magic really starts to happen when you add custom tabs and connectors.
If you had a channel concerning the delivery of a project to a customer, you might have a tab which had the original proposal. You might have another tab holding a live Microsoft Planner document that everyone can share and keep up-to-date. Perhaps a tab containing a OneNote notebook so that you can see field sales’ notes in real time. Another tab might contain a Microsoft Form to be completed to then trigger other actions.
There is a rapid growth of third-party tools appearing in the Teams store to bring in data and functionality from apps you already use such as Trello, Smartsheet, SurveyMonkey, Evernote, Wrike, social networks and more. For example, in our Marketing team general channel we have the Mailchimp connector installed, which means “the chimp” drops in to the chat regularly with a report on the performance of our latest campaigns. The possibilities are pretty endless!

It also does the Skype thing
Teams has replaced Skype for Business and improves on its predecessor:
- One to one and group online audio and video calls
- Screen sharing
- Instant online meetings and presentations
- Scheduled meetings for up to 300 people (meaning arranged ahead of time)
- Meeting polls and hand-raising
- Breakout rooms *
- Meeting recording *
- Phone calls and audio conferencing *
* Not available in the free version
How do I get Microsoft Teams?
If you already have an Microsoft 365 subscription, you most likely already have Microsoft Teams. Visit https://teams.microsoft.com and sign in.
If not, there are numerous ways to get Teams. The best choice depends on your needs and the type of business you work with. Give us a call to discuss.
iBizify can help
iBizify have been helping its clients make the best of Microsoft 365 since 2012, providing specialist setup, email and data migration, support and training services based on the world’s best business productivity platform.
To discuss how you can benefit please get in touch.
Blog
- Don’t get phished!
- How to set up Microsoft Authenticator
- Understanding your Microsoft 365 email quarantine
- Development and consultancy hours - simplified
- We have a new logo
- We have moved
- What to look for in a PC for your small business
- Why you should get to know Microsoft Teams
- Making a splash with Acorn Commercials
- Case study: Tavistock House Dental Practice
- Steve raised over £685 for Marie Curie
- SEO, Spam, Cowboys & Indians
- What is the “Cloud” all about?
- Why do we need the Cloud?
- Learning to be a regular Tippler
- Are you a Binger, Regular Tippler or Abstainer?
- What are ‘hits’? (web analytics and statistics)